Proxied Access to Network-Restricted Clusters

Enabling a proxied access allows you to access Attached and Managed clusters that are network-restricted, in a private network, firewalled, or at edge.
This section only applies to clusters with networking restrictions that were attached through a secure tunnel.
You can attach clusters that are in a private network (clusters that have networking restrictions or are at the edge). D2iQ provides the option of using a secure tunnel or a tunneled attachment to attach a Kubernetes cluster to the Management cluster. To access these attached clusters through kubectl or monitor its resources through the Management cluster, you have to be in the same network, or enable a proxied access.
Proxied Access
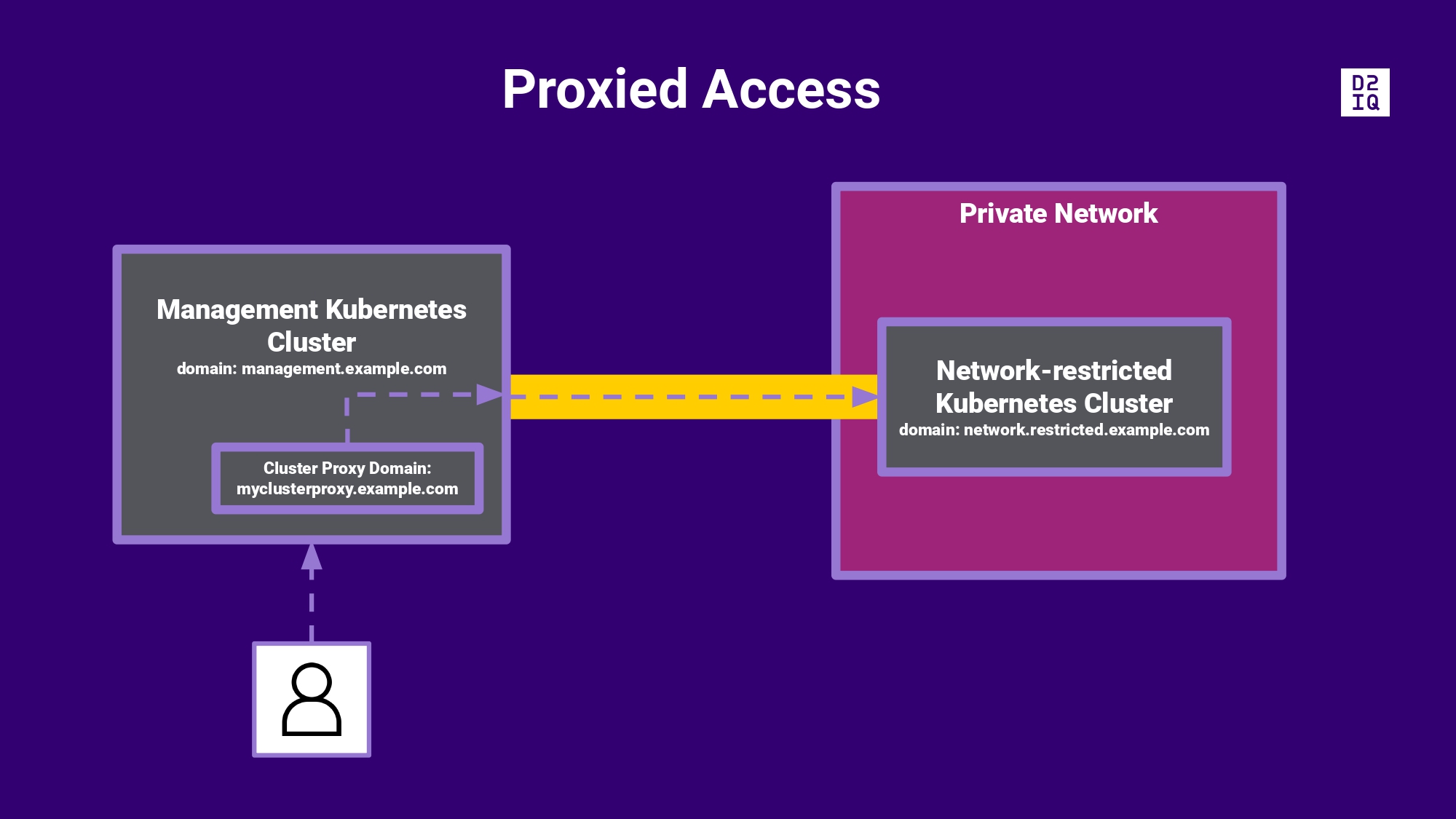
Access to a network-restricted cluster through a proxy in the Management cluster
Enabling the proxied access for a network-restricted cluster makes it possible for DKP to authenticate user requests (regardless of the identity provider) through the Management cluster’s authentication proxy. This is helpful, when the cluster you are trying to reach is in a different network. The proxied access allows you to:
Access and observe the cluster’s monitoring and logging services from the Management cluster, for example:
Access the cluster’s Grafana, Kubernetes and Kubecost dashboards from the Management cluster.
Use the CLI to print a cluster’s service URL, so you can access the cluster’s dashboards.
Access and perform operations on the network-restricted cluster from the Management cluster, for example:
Generate an API token (Generate Token option, from the upper right corner of the UI) that allows you to authenticate to the network-restricted cluster.
Upon authentication, use
kubectlto manage the network-restricted cluster.
You can perform the previous actions, without being in the same network as the network-restricted cluster.
.png)