Multi-Tenancy in DKP
What Is Multi-Tenancy?
You can use workspaces to manage your tenants' environments separately, while still maintaining control over clusters and environments centrally. For example, if you operate as a Managed Service Provider (MSP), you can manage your clients clusters' lifecycles, resources, and applications. If you operate as an environment administrator, you can these resources per department, division, employee group, etc.
Here are some important concepts:
How Does Access Control Work in Multi-Tenant Environments?
To isolate each tenant’s information and environment, multi-tenancy allows you to configure an identity provider per workspace or tenant. In this setup, DKP keeps all workspaces and tenants separate and isolated from each other.
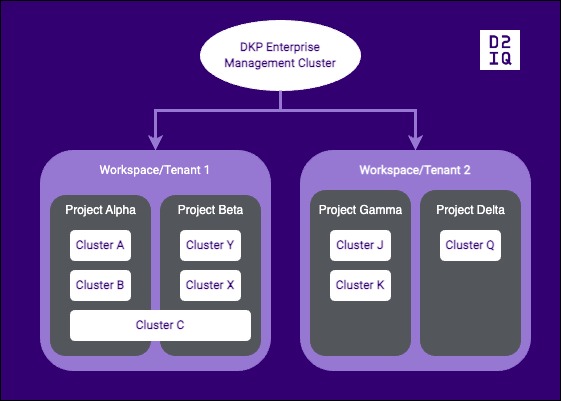
Multi-tenancy example with one Management cluster, and two tenants.
You, as a global administrator, manage tenant access at the Workspace level. A tenant can further adapt user access at the Project level.
How Do I Enable Multi-Tenancy?
To enable multi-tenancy, you must:
Configure an Identity Provider globally, if you want to use a single IdP to access all of your tenant’s environments.
Configure an Identity Provider per workspace. This way, each tenant has a dedicated IdP to access their workspace.
Create DKP Identity Provider groups with the correct prefixes to map your existing IdP groups.
Create a dedicated login URL for each tenant. You can provide a workspace login link to each tenant for access to the DKP UI and for the generation of kubectl API access tokens.
To enforce security, every tenant should be in a different AWS account, so they are truly independent of each other.
.png)