Traefik-Forward-Authentication in DKP (TFA)
TFA Overview
Traefik-Forward-Authentication (TFA) is a vital component in DKP. It handles authentication and authorization of web (HTTP) requests and how users can access the DKP UI. Regardless of the authentication method you choose (user and password, SSO, 2FA, etc.), TFA is a component that authorizes HTTP clients to enter your environment.
TFA is one of the standard applications in the Kommander component of DKP. It is deployed by a controller on all attached, managed, and management clusters.
TFA Authentication Workflow
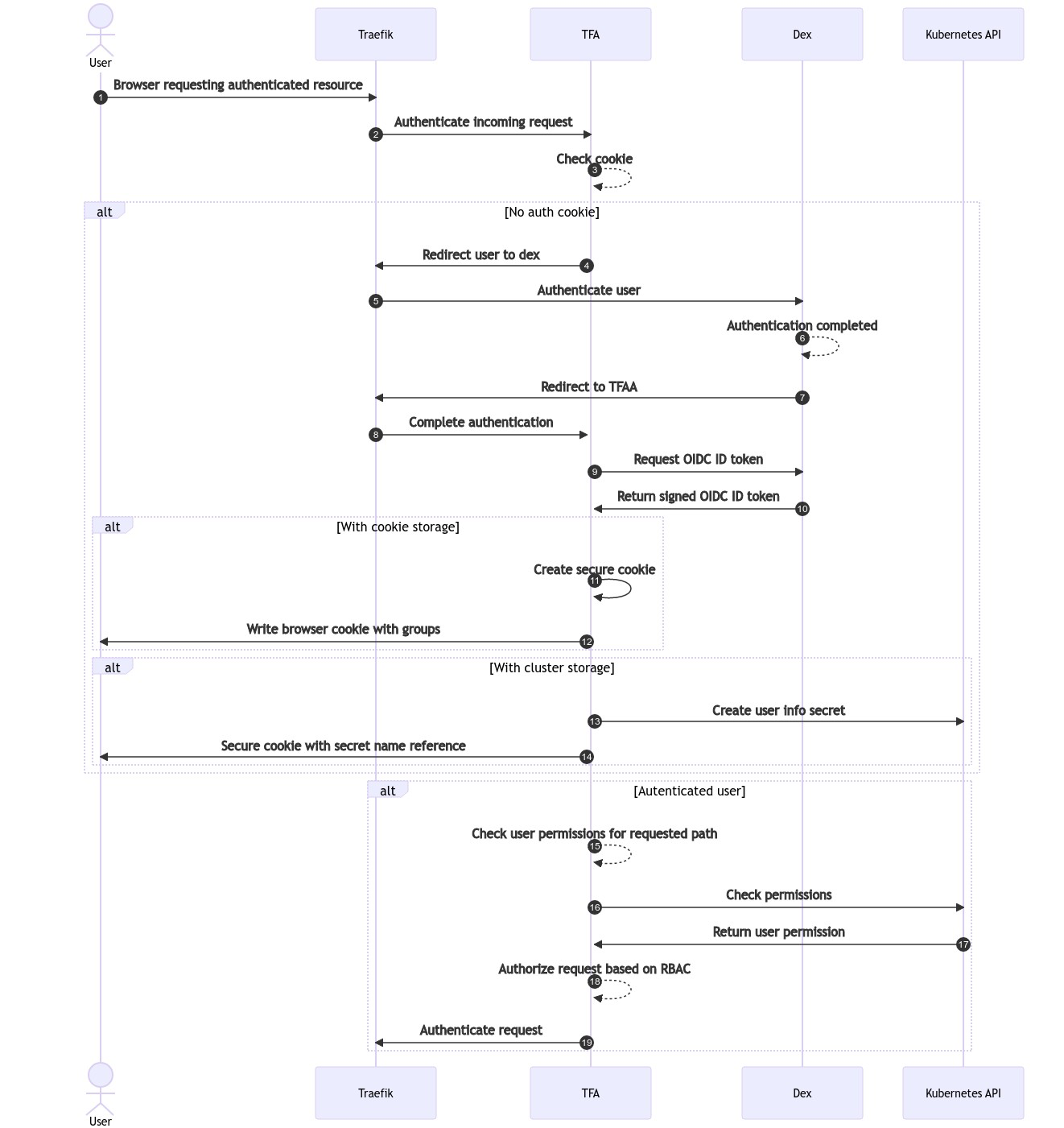
Default TFA Configuration in DKP
In the default configuration in DKP, TFA stores all authentication information about users via the browser cookies. When TFA authenticates users, it stores the user’s metadata in encrypted browser cookies. Subsequent requests following initial authentication will use these cookies to recognize users without the need to re-authenticate them.
NOTE:
The cookies are securely encrypted, so they cannot be modified by users.
The cookies contain the RBAC username.
The cookies contain a list of groups that users are associated with.
Cluster Storage Option
The browser cookie storage is limited to a maximum of 4Kb per cookie. However, if a user is assigned to a large number of groups, this limitation can be exceeded and this will return a response 500-internal server error, meaning that the user will be unable to access any web services.
To work around the cookie storage size limit, TFA can be configured to store the metadata claims in the cluster as a Kubernetes secret instead of in the browser. To do so, the clusterStorage option can be configured in the Traefik Forward Auth application when installing Kommander.
In order to enable the clusterStorage option, add the following to the cluster.yaml when installing Kommander:
traefik-forward-auth-mgmt:
values: |
clusterStorage:
enabled: true
namespace: kommander
If the clusterStorage feature is enabled, automatic garbage collection will delete the secrets after 12 hours. Keep in mind that enabling this feature will have performance implications for web requests, because TFA needs to load the secret to retrieve the user groups for each HTTP API request. Because of this, we recommend first trying to reduce the number of groups associated users and only enabling this option if that cannot be accomplished.
For additional information about traefik-forward-authentication, see the TFA page on Github.
.png)