Project Roles

Project Roles are used to define permissions at the namespace level.
Configure Project Role - UI Method
In the example below, a Project Role is created with a single Rule. This Project Role corresponds to an admin role.
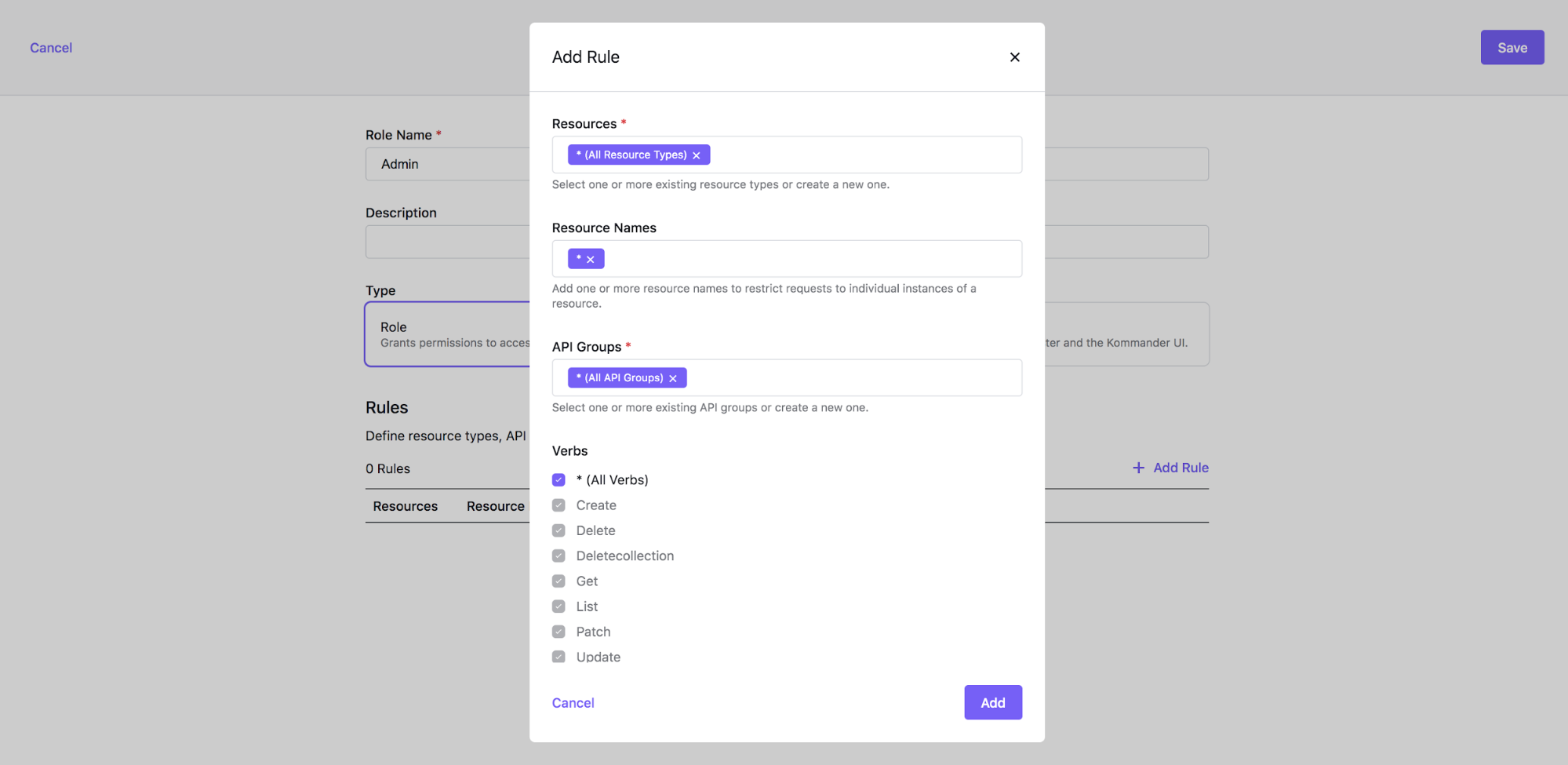
You can create a Project Role with several Rules.
Configure Project Role - CLI Method
The same Project Role can also be created using kubectl:
cat << EOF | kubectl create -f -
apiVersion: workspaces.kommander.mesosphere.io/v1alpha1
kind: ProjectRole
metadata:
annotations:
kommander.mesosphere.io/display-name: Admin
generateName: admin-
namespace: ${projectns}
spec:
rules:
- apiGroups:
- '*'
resources:
- '*'
verbs:
- '*'
EOFEnsure the projectns variable is set before executing the command.
You can set it using the following command (for a Kommander Project called project1, and after setting the workspacens as explained in the previous section):
projectns=$(kubectl -n ${workspacens} get projects.workspaces.kommander.mesosphere.io -o jsonpath='{.items[?(@.metadata.generateName=="project1-")].status.namespaceRef.name}')When a Project Role is created, Kommander creates a Kubernetes FederatedRole on the Kubernetes cluster where Kommander is running:
kubectl -n ${projectns} get federatedroles.types.kubefed.io admin-dbfpj-l6s9g -o yaml
apiVersion: types.kubefed.io/v1beta1
kind: FederatedRole
metadata:
creationTimestamp: "2020-06-04T11:54:26Z"
finalizers:
- kubefed.io/sync-controller
generation: 1
name: admin-dbfpj-l6s9g
namespace: project1-5ljs9-lhvjl
ownerReferences:
- apiVersion: workspaces.kommander.mesosphere.io/v1alpha1
blockOwnerDeletion: true
controller: true
kind: ProjectRole
name: admin-dbfpj
uid: e5f3b2ca-16bf-474d-8305-7be04c034793
resourceVersion: "75680"
selfLink: /apis/types.kubefed.io/v1beta1/namespaces/project1-5ljs9-lhvjl/federatedroles/admin-dbfpj-l6s9g
uid: 1e5a3d98-b223-4605-bba1-16276a3eb47c
spec:
placement:
clusterSelector: {}
template:
rules:
- apiGroups:
- '*'
resourceNames:
- '*'
resources:
- '*'
verbs:
- '*'
status:
clusters:
- name: konvoy-5nr5h
conditions:
- lastTransitionTime: "2020-06-04T11:54:26Z"
lastUpdateTime: "2020-06-04T11:54:26Z"
status: "True"
type: Propagation
observedGeneration: 1Then, if you run the following command on a Kubernetes cluster associated with the Project, you see a Kubernetes Role object in the corresponding namespace:
kubectl -n ${projectns} get role admin-dbfpj-l6s9g -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
creationTimestamp: "2020-06-04T11:54:26Z"
labels:
kubefed.io/managed: "true"
name: admin-dbfpj-l6s9g
namespace: project1-5ljs9-lhvjl
resourceVersion: "29218"
selfLink: /apis/rbac.authorization.k8s.io/v1/namespaces/project1-5ljs9-lhvjl/roles/admin-dbfpj-l6s9g
uid: f05b998c-4649-4e73-bbfe-c12bc4c86a3c
rules:
- apiGroups:
- '*'
resourceNames:
- '*'
resources:
- '*'
verbs:
- '*'.png)